Bring your device (BYOD) refers to the policy of allowing employees to use their devices like smartphones, laptops, and tablets for work purposes.
BYOD policies aim to boost productivity by enabling employees to access company data and applications on the go. However, they also pose cybersecurity risks if not managed properly.
This article will explain what BYOD is, how it works, popular tools and strategies, how to develop a BYOD policy, pros and cons, and frequently asked questions.
Embracing BYOD can empower your workforce but requires thoughtful planning to keep company data secure.

Key Points on BYOD
- BYOD policies first emerged around 2009 when mobile devices like smartphones and tablets became mainstream.
- It was a shift from traditional “corporate-liable” policies where companies issued standardized devices to employees.
- BYOD policies apply to mobile devices as well as portable computers like laptops.
- BYOD aims to boost productivity, flexibility, and job satisfaction by allowing employees to use their own familiar devices.
- But BYOD also raises security risks of company data on personal devices that organizations must mitigate.
How Does a BYOD Policy Work?
For a BYOD policy to work, organizations need strategies and tools to manage access, security, apps, content, and expenses:
1. Access management:
- Employees are granted access to company networks with their devices.
- Multi-factor authentication ensures that only authorized users can access sensitive data.
- Mobile device management (MDM) tools enroll and manage devices.
2. Security:
- Endpoint security tools like antivirus safeguard devices.
- Encryption protects sensitive data stored on devices.
- Remote wipe capabilities help secure lost or stolen devices.
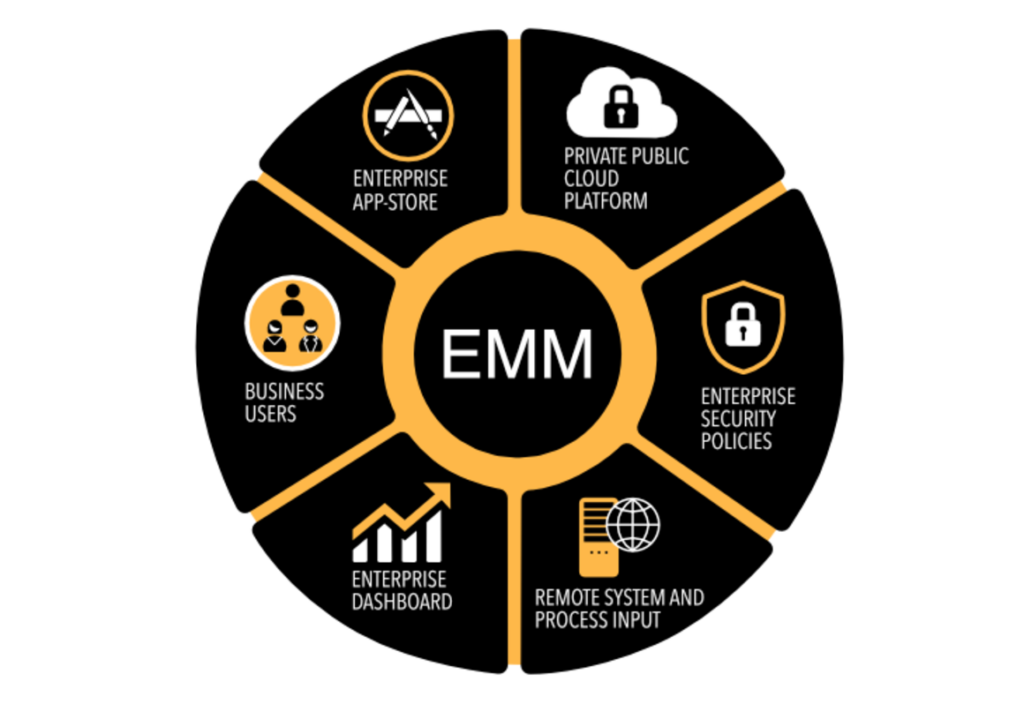
- VPNs keep data secure when accessing company networks via public Wi-Fi.
3. Apps and content:
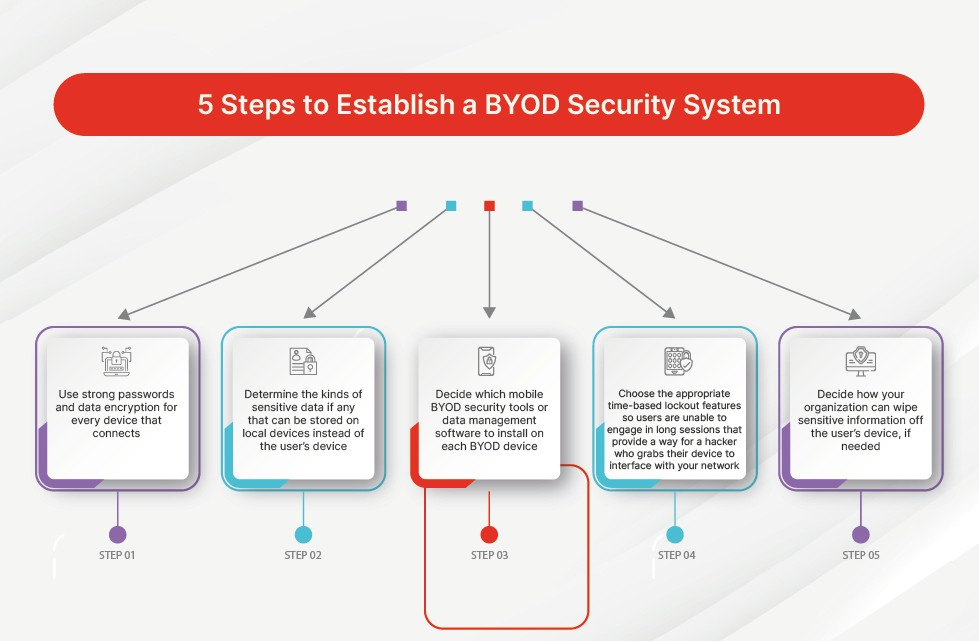
- Enterprise mobility management (EMM) tools deploy apps and content to BYOD devices.
- Containerization separates work and personal apps and data on the device.
4. Expense management:
- Companies may implement cost-sharing plans to subsidize equipment and service costs.
- Stipends reimburse employees for using personal devices and data plans for work.
Most Popular BYOD Tools and Device Management Strategies
Organizations rely on various BYOD-friendly software, platforms, and strategies to manage personal devices and secure corporate data:
1. Mobile Device Management (MDM)
MDM tools like VMWare AirWatch enroll devices to apply security policies, deploy apps/settings, and remotely manage devices. MDM helps secure and control BYOD at scale.
2. Mobile Application Management (MAM)
MAM tools like Apperian and Appaloosa let you build and deploy custom mobile apps. This allows BYOD users to access business apps without compromising security.
3. Enterprise Mobility Management (EMM)
EMM suites like Microsoft Intune combine MDM for device management with MAM for app management. This provides comprehensive BYOD management.
4. Virtualization
Solutions like Citrix XenMobile separate personal and work environments on BYOD devices via virtualization. This helps keep business and personal apps and data apart.
5. Containerization
Apps like Samsung Knox create encrypted containers on devices for work data and apps. This securely separates them from personal content.
6. Remote wiping
BYOD management software allows remote wipe capabilities to delete company data from lost or compromised devices while leaving personal data intact.
7. VPN
Virtual Private Networks (VPNs) like Cisco AnyConnect encrypt data and obscure traffic, protecting company networks and data as employees access them from personal devices.
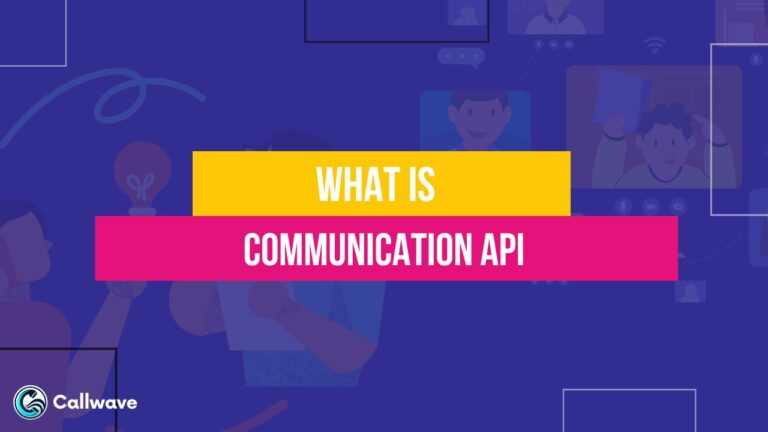
How to Develop Your BYOD Policy?
Crafting a BYOD policy involves evaluating your needs, outlining appropriate usage guidelines, selecting technology, training employees, and enforcing protocols. Key steps include:
1. Identify Goals
Consider the benefits you hope to achieve from allowing BYOD like productivity, satisfaction, and mobility. Also, identify any concerns like security risks.
2. Outline Approved Devices and Usage Guidelines
Specify which employee-owned devices are approved for BYOD based on their security features and business capabilities. Outline appropriate use expectations.
3. Select Management Tools
Research and select MDM, MAM, EMM, and other tools to manage BYOD devices and apps. Enforce encryption, passwords, wiping, etc.
4. Develop Security Policies
Establish security policies like required antivirus, prohibited usage, access controls, and data protection. Address issues like jailbreaking, rooting, and unauthorized access.
5. Create Protocols for Data Ownership, Privacy, Support
Outline who owns data on BYOD devices. Detail privacy standards for monitoring and controlling personal devices. Specify IT support policies for employee devices.
6. Implement Training and Awareness Programs
Inform employees about BYOD usage guidelines, security protocols, and expectations through training. Promote safe BYOD practices.
7. Deploy Resources and Finalize Logistics
Distribute resources like apps, network settings, and device guidelines to employees. Finalize expense reimbursement logistics and cost-sharing programs.
8. Monitor and Refine
Monitor BYOD usage, challenges, and benefits. Refine policies and procedures as needed to improve the program over time.
The Pros and Cons of BYOD
BYOD offers benefits but also poses significant risks that organizations must weigh:
Pros:
- Increased productivity – Employees can work flexibly from their familiar, preferred device.
- Greater job satisfaction – People enjoy using their own chosen, customized device.
- Cost reduction – Companies don’t have to purchase and manage devices for employees.
- Environmental benefits – BYOD extends the useful life of employee-owned devices.
Cons:
- Security risks – Personal devices expose business data to risks of loss, theft, and unauthorized access.
- Support difficulties – Supporting many different devices is challenging and expensive for IT teams.
- Compliance concerns – BYOD makes device monitoring and data protection more difficult.
- Blurred boundaries – BYOD can lead to an “always on” work culture with unclear personal/professional divisions.
- Equity issues – Allowances or stipends may be perceived as inequitable if not structured appropriately.
Frequently Asked Questions (FAQ)
Ques 1: What kinds of devices are typically allowed under BYOD policies?
Ans: Most BYOD policies allow smartphones (iOS, Android), tablets (iPads, Android), and laptops (Windows, MacOS). Less commonly, wearables and other IoT devices may be permitted.
Ques 2: Can companies monitor or manage employee-owned devices?
Ans: Yes, companies can monitor and manage devices to varying degrees via MDM, MAM, and EMM tools. However, they must respect employee privacy and limit overreach.
Ques 3: Who is responsible for the security, support, and maintenance of BYOD devices?
Ans: Employees retain ownership duties for their devices. However, companies are responsible for implementing security policies to protect corporate data on BYOD equipment.
Ques 4: Can companies remotely wipe BYOD devices?
Ans: Yes, most BYOD programs allow IT to selectively and remotely wipe company data from BYOD devices without deleting personal content.
Ques 5: Do employees need to agree to any BYOD policy terms?
Ans: Yes, employees should review and consent to BYOD policies so rights, responsibilities, and restrictions are clear. Companies should have employees acknowledge policies.