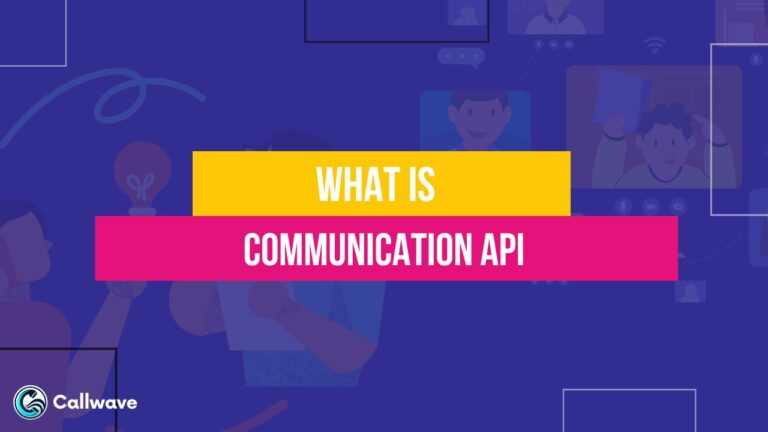
VoIP is a technology that allows you to make voice calls over the internet instead of using traditional phone lines.
When you make a VoIP call, your voice is converted into digital data packets and transmitted over the internet to the recipient’s device, where it’s converted back into audio.
Now, the thing about the internet is that it’s a public network, which means that your data packets can potentially be intercepted by anyone along the way. This is where encryption comes into play.

What is VoIP Encryption?
Encryption is like a secret code that scrambles your data so that only the intended recipient can unscramble and understand it.
It’s like putting your voice data into a locked box, and only you and the person you’re calling have the key to unlock it.
Without encryption, anyone who manages to intercept your VoIP data packets could potentially listen in on your conversations or even manipulate the data.
This is a major privacy and security concern, especially for businesses or individuals discussing sensitive information.
VoIP encryption works by applying complex mathematical algorithms to your voice data before it’s transmitted over the internet.
These algorithms essentially scramble the data into an unreadable format, making it incredibly difficult for anyone without the proper decryption key to make sense of it.
Different VoIP providers and services use different encryption methods, but some of the most common ones are:
- Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP): These are widely used encryption protocols that secure the entire communication channel between the caller and the recipient.
- Advanced Encryption Standard (AES): This is a powerful encryption algorithm that can effectively scramble data, making it virtually impossible to crack without the correct key.
The strength and effectiveness of VoIP encryption can vary depending on the encryption methods used, the key lengths, and the overall implementation.
It’s essential to choose a reputable VoIP service provider that prioritizes security and uses robust encryption methods to protect your privacy and safeguard your communications.
What is End-To-End Encryption?
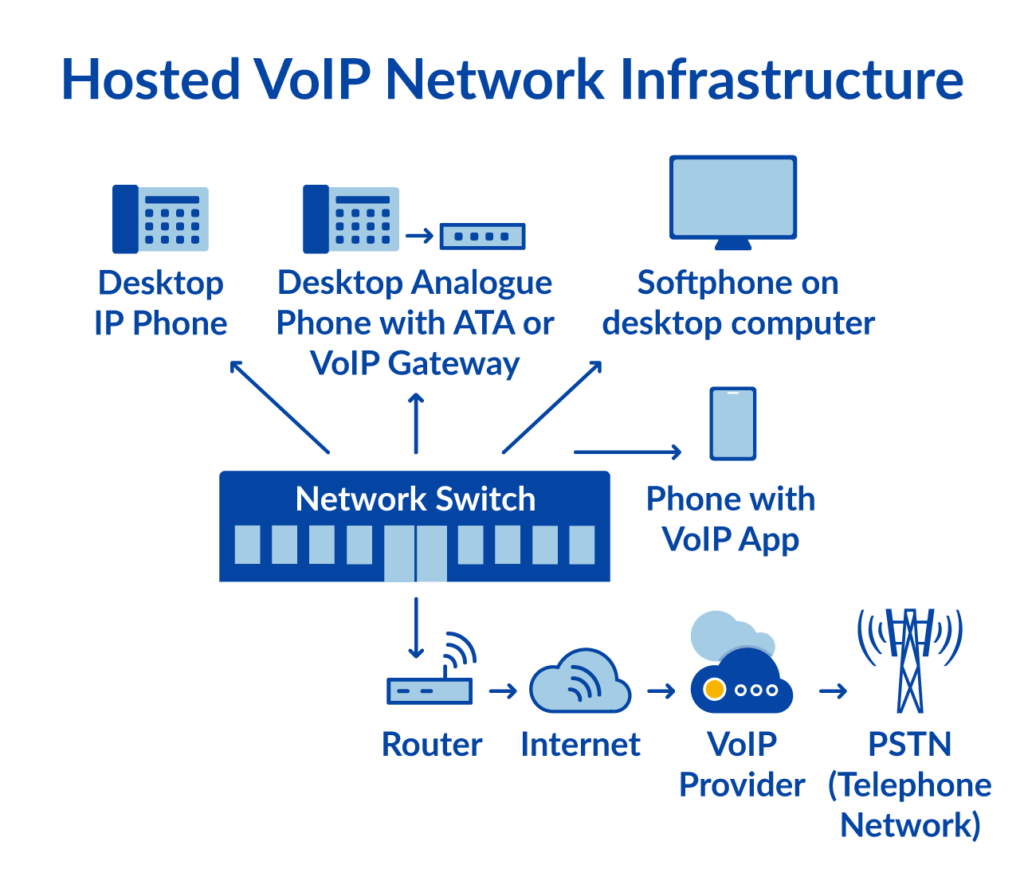
End-to-end encryption is a secure communication method where only the communicating parties can access the data being transmitted.
The data is encrypted on the sender’s device and can only be decrypted by the recipient’s device using a unique encryption key.
This means that even the service provider or any intermediary cannot access the unencrypted data during transmission.
End-to-end encryption ensures that communications remain private and secure, even if the communication channels are compromised.
It provides the highest level of security for sensitive data exchange, such as messaging, voice calls, and video conferencing.
Types of VoIP Security Risks
1. Packet Sniffing
When someone intercepts and captures the data packets being transmitted during a VoIP call, it is called packed sniffing.
It’s like someone eavesdropping on your conversation by tapping into the network. Packet sniffers can be used to steal sensitive information, like login credentials or credit card numbers.
How to prevent it: Use encryption to scramble the data packets, making them unreadable to anyone who intercepts them. Implement strong access controls and firewalls to restrict unauthorised access to your network.
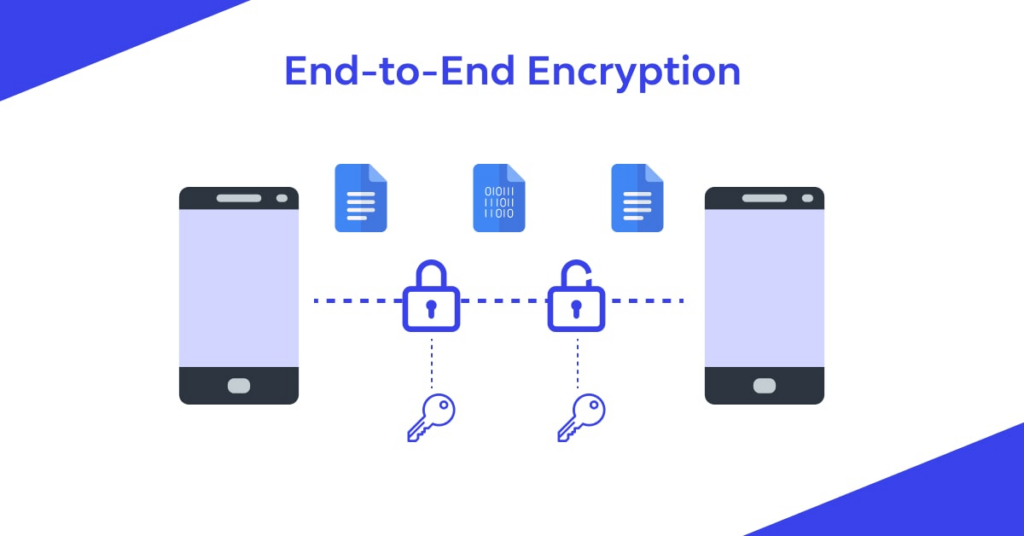
2. DDoS Attack
A Distributed Denial of Service (DDoS) attack is when multiple compromised systems flood a VoIP server or network with overwhelming traffic, causing it to become overloaded and crash.
It’s like having too many people trying to enter a room at once, causing a blockage and preventing anyone from getting in.
How to prevent it: Implement DDoS mitigation strategies, such as traffic monitoring, load balancing, and filtering suspicious traffic. Also, keep your systems and software up-to-date with the latest security patches.
3. Ransomware
Ransomware is a type of malicious software that encrypts your data and holds it hostage until you pay a ransom to regain access.
It’s like someone breaking into your house, stealing your valuables, and demanding money to get them back.
How to prevent it: Regularly back up your data, keep your systems updated with the latest security patches, and educate your employees on recognizing and avoiding suspicious emails or links that could contain ransomware.
4. Vishing
Vishing, or voice phishing, is a type of social engineering attack where scammers try to trick you into revealing sensitive information over a VoIP call.
It’s like someone calling you and pretending to be from a legitimate company, trying to get you to share your login credentials or credit card details.
How to prevent it: Educate yourself and your employees on recognizing vishing attempts, and never share sensitive information over the phone unless you’ve verified the caller’s identity and the legitimacy of the request.
5. Malware and Viruses
Malware and viruses are malicious software designed to harm or disrupt computer systems.
In the context of VoIP, they can be used to gain unauthorized access to your network, steal data, or disrupt your communications.
How to prevent it: Install and regularly update antivirus and anti-malware software, avoid downloading files or clicking on links from untrusted sources, and educate your employees on recognizing and avoiding potential malware threats.
6. Phreaking Attack
Phreaking is a type of hacking attack where someone tries to gain unauthorized access to a VoIP system or network, often by exploiting vulnerabilities or weaknesses in the system’s security.
How to prevent it: Keep your VoIP software and systems up-to-date with the latest security patches, implement strong access controls and firewalls, and regularly monitor your network for any suspicious activity or unauthorized access attempts.
7. SPIT (Spam over Internet Telephony)
SPIT is the VoIP equivalent of email spam, where unwanted pre-recorded messages or calls are sent to VoIP numbers.
It’s like receiving annoying telemarketing calls, but over your internet-based phone system.
How to prevent it: Implement SPIT filtering and blocking technologies, such as blacklists, whitelists, and caller authentication, to help identify and block unwanted calls.
8. Man-in-the-Middle Attacks
In a man-in-the-middle attack, a hacker inserts themselves between the two parties communicating over a VoIP call, intercepting and potentially manipulating the data being transmitted.
It’s like having someone listening in on your conversation and potentially altering what’s being said.
How to prevent it: Use end-to-end encryption to secure your VoIP communications, and implement strong authentication methods to verify the identities of the communicating parties.
9. Toll Fraud
Toll fraud occurs when someone gains unauthorized access to your VoIP system and makes long-distance or premium-rate calls at your expense.
It’s like someone breaking into your house and using your phone to make expensive calls, leaving you with the bill.
How to prevent it: Implement strong access controls, regularly monitor your VoIP system for any suspicious activity or unusual call patterns, and consider implementing toll fraud prevention solutions offered by your VoIP provider.
10. Call Tampering
Call tampering is when someone intercepts and alters the data being transmitted during a VoIP call, potentially changing the content of the conversation or injecting unwanted audio or video.
How to prevent it: Use end-to-end encryption to secure your VoIP communications, and implement strong authentication methods to verify the identities of the communicating parties.
11. VOMIT (Voice over Misconfigured Internet Telephony)
VOMIT refers to security vulnerabilities and misconfigurations in VoIP systems that can be exploited by attackers to gain unauthorized access, disrupt services, or intercept communications.
How to prevent it: Regularly review and update your VoIP system configurations, follow best practices for secure setup and deployment, and stay up-to-date with the latest security advisories and patches from your VoIP provider.
Remember, the key to protecting your VoIP communications is to implement a multi-layered security approach, including encryption, access controls, firewalls, and regularly updating your systems and software.

Best Practices for VoIP Security
- Encryption is Key: Always use strong encryption protocols like TLS (Transport Layer Security) and SRTP (Secure Real-time Transport Protocol) to scramble your VoIP data. This makes it virtually impossible for anyone to snoop on your conversations, even if they manage to intercept the data packets.
- Keep Software Updated: Regularly update your VoIP software, operating systems, and any related applications or plugins. These updates often include critical security patches that fix vulnerabilities and protect you from the latest threats.
- Implement Access Controls: Use strong authentication methods, such as multi-factor authentication, to verify the identities of users accessing your VoIP system. Additionally, restrict access to only those who need it and regularly review and update access privileges.
- Secure Your Network: Implement firewalls, intrusion detection/prevention systems, and virtual private networks (VPNs) to secure your network and protect it from unauthorized access or malicious attacks.
- Monitor and Log Activities: Regularly monitor your VoIP system for any suspicious activities or unusual call patterns. Enable logging and review the logs periodically to detect and respond to potential security incidents promptly.
Remember, security is a shared responsibility.
By implementing these best practices within your organization, you can significantly reduce the risks associated with this technology and enjoy reliable communications.
Most Secure VoIP Software
| Provider | Uptime | End-to-End Encryption | Support Hours | HIPAA Compliance | ISO-27001 Certification and SOC 2 Compliance | Independent Security Audits |
| 8×8 | 99.99% | Yes | 24/7 | Yes | Yes | Yes |
| RingCentral | 99.999% | Yes | 24/7 | Yes | Yes | Yes |
| Nextiva | 99.99% | Yes | 24/7 | Yes | Yes | Yes |
| Vonage | 99.99% | Yes | 24/7 | Yes | Yes | Yes |
| GoTo Connect | 99.99% | Yes | 24/7 | Yes | Yes | Yes |
Let’s understand the parameters that were taken into consideration to rate these services:
Uptime: This refers to the percentage of time the VoIP service is operational and available. All five providers offer excellent uptime rates of 99.99% or higher.
End-to-End Encryption: This indicates whether the provider offers end-to-end encryption for VoIP calls, ensuring that only the communicating parties can access the data. All five providers offer end-to-end encryption.
Support Hours: This shows the availability of customer support services. All five providers offer 24/7 support.
HIPAA Compliance: This indicates whether the provider’s services are compliant with the Health Insurance Portability and Accountability Act (HIPAA) regulations, which is essential for healthcare organizations handling sensitive patient data. All five providers are HIPAA-compliant.
ISO-27001 Certification and SOC 2 Compliance: These are industry-standard certifications and compliance measures that demonstrate the provider’s commitment to information security management and data protection. All five providers have obtained these certifications and are compliant with these standards.
Independent Security Audits: This indicates whether the provider subjects its services and infrastructure to regular independent security audits by third-party auditors. All five providers undergo independent security audits.
It’s worth noting that while all five providers excel in terms of security and encryption features, your specific requirements and preferences may influence your choice.
It’s advisable to thoroughly evaluate each provider’s offerings, pricing, and additional features to determine the best fit for your organization.
FAQs
Ques 1: What is VoIP in cyber security?
A1: VoIP in cyber security refers to the security risks and vulnerabilities associated with internet-based voice communications.
Ques 2: Are VoIP lines secure?
A2: VoIP lines are not inherently secure, as the data travels over the public internet. Proper encryption and security measures are necessary.
Ques 3: What protocol protects VoIP?
A3: Protocols like SRTP (Secure Real-time Transport Protocol) and TLS (Transport Layer Security) are used to protect VoIP communications.
Ques 4: Can VoIP calls be tapped?
A4: Yes, unencrypted VoIP calls can be tapped or intercepted if proper security measures are not implemented.
Ques 5: How do I encrypt a VoIP call?
A5: You can encrypt a VoIP call by using end-to-end encryption protocols like SRTP or TLS.