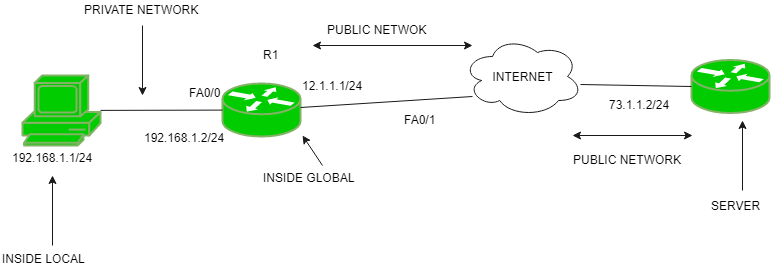
NAT is a method of mapping multiple private IP addresses used within an internal network to a public IP address used on the Internet.
NAT allows a single device, usually a router, to act as an agent between the Internet and a local network.
This allows a company or home network to use a private IP address scheme within their internal network while still being able to reach the wider Internet.
NAT traversal refers to techniques that establish and maintain Internet protocol connections in the presence of NAT devices.
This is necessary for end-to-end connectivity between hosts located behind NAT devices. NAT traversal techniques are required for many Internet applications, including peer-to-peer applications, voice-over IP, multiplayer online games, and virtual private networks.
Why NAT is Used?
There are two main reasons NAT is used:
- To enable multiple devices to access the Internet using a single public IPv4 address. This preserves the limited public IPv4 address space. IPv4 provides for about 4 billion addresses, which is not enough for all the devices connecting to the Internet. NAT enables ISPs to use private addresses within their network while assigning just one public address to each customer. This allows many more devices to connect.
- To enhance network security by obscuring device addresses on the internal network. Publicly routing these private addresses would allow direct access to those devices from the Internet. By using NAT, only the public address of the router is visible externally, protecting the directly connected devices. This provides a basic firewall capability.
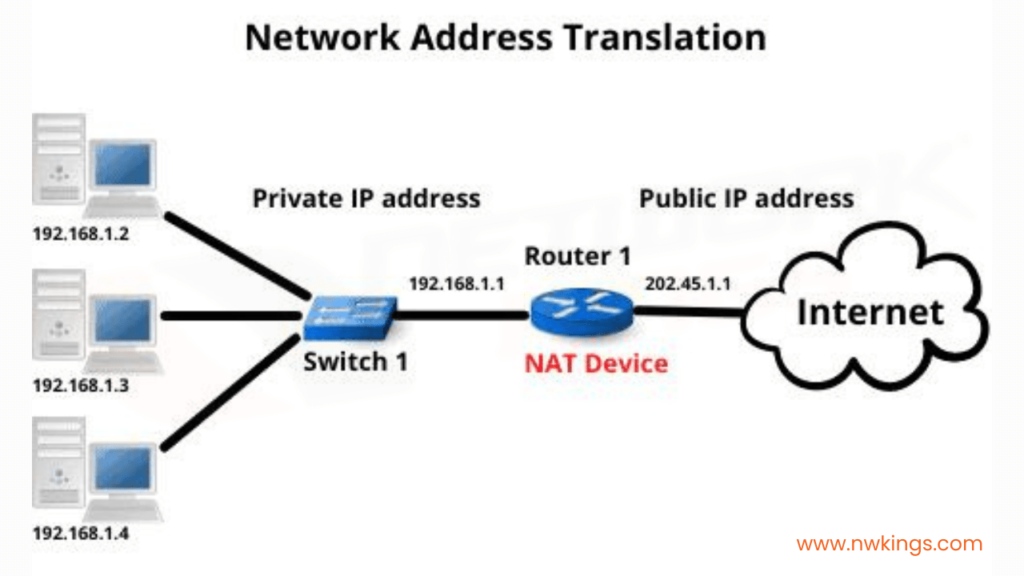
How does NAT work?
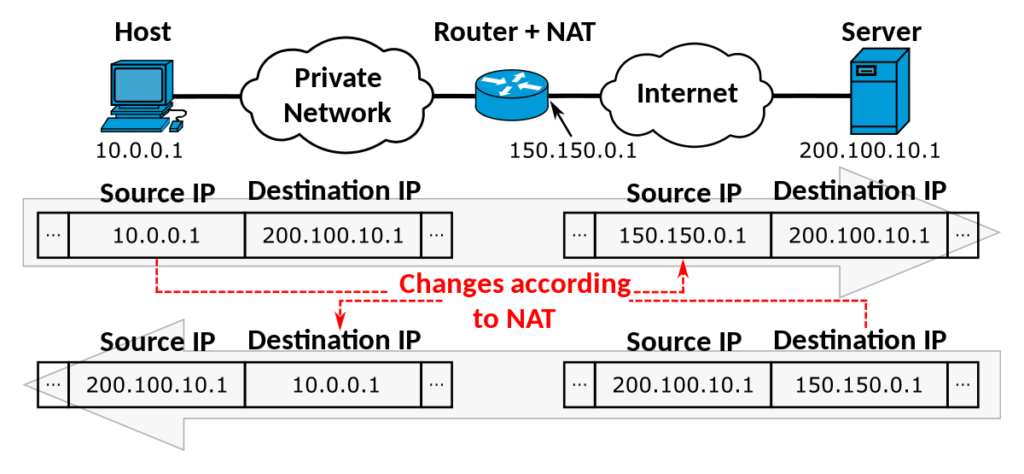
When a device on the internal network sends out a request to the Internet, the NAT device (usually a router or firewall):
- Substitutes its public IP address for the private IP address of the sending device. This masks the internal device’s IP address from external network devices.
- Assign a temporary port number to the connection. This keeps each connection distinct.
- Records this mapping from private IP and port to public IP and port in a NAT translation table.
When the response comes back, the NAT device checks the translation table to forward the traffic to the correct internal device and port using the private IP address.
This allows internal devices to communicate with the outside world while obscuring the actual private IP addresses they use.
Types of NAT
There are 4 basic types of NAT provided for in RFC 1631:
- Full Cone NAT – Once an internal address is mapped to an external address, any external host can send packets to that external address.
- Restricted Cone NAT – An external host can send packets to a particular external address only if the internal host has first sent a packet to that particular external address.
- Port Restricted Cone NAT – Functions like a restricted cone NAT, but also requires the external port on the external host to be the same as the port used by the internal host when it first sent a packet to that external address.
- Symmetric NAT – Each request from the same internal IP and port to a specific external IP and port is mapped to a unique external source IP and port. External hosts can only send packets to the internal host by responding to packets it first sent out.
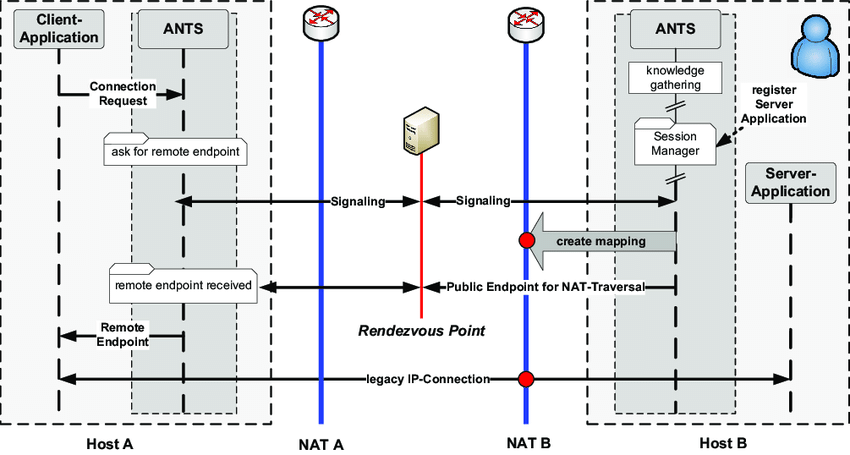
NAT Traversal Techniques
Since NAT obscures the source IP addresses and ports of devices on the internal network, protocols and applications that embed IP addresses in their messages can break.
Special techniques called NAT traversal establish and maintain connections through NAT devices. Common NAT traversal techniques include:
- NAT Hole Punching – Applications try to establish connections from both sides so NAT devices open up ports and create table entries allowing data to flow end-to-end.
- Application Layer Gateways (ALGs) – NAT routers are configured with ALGs that inspect application layer traffic and rewrite IP addresses and ports in the payload to make protocols like FTP work across NAT.
- UPnP and PCP – Universal Plug and Play (UPnP) and Port Control Protocol (PCP) allow applications to directly interact with the NAT device to open ports and map connections.
- STUN and TURN – STUN servers determine the public IP and ports required. If that fails, TURN servers relay traffic, acting as a middleman to enable connectivity.
- VPNs – Virtual Private Networks (VPNs) encapsulate traffic in another IP header to enable routing through NAT devices.
Advantages of NAT
Some key advantages of NAT include:
- Conserves public IPv4 addresses – NAT enables many devices to share a single public IP address, slowing IPv4 address exhaustion.
- Facilitates IPv4 to IPv6 transition – NAT allows a gradual transition to IPv6 by providing IPv4 access.
- Added security – NAT hides internal IP addresses from the public Internet, preventing direct attacks.
- Shields network changes – With NAT, you can change internal IP addressing schemes without impacting external systems.
- Centralized logging and policy control – NAT enables centralized control of connectivity and logging at the NAT router or firewall.
- Ease of setup – For home networks, NAT is built into most router firmware, providing plug-and-play connectivity.
- Facilitates client transition – NAT allows upgrades of internal clients without immediately upgrading Internet servers.
Disadvantages of NAT
Some potential disadvantages to using NAT include:
- Loss of end-to-end connectivity – NAT breaks end-to-end connectivity, preventing unique identification of devices.
- NAT traversal complexity – Applications must use NAT traversal techniques to establish and maintain connections.
- Deprecates IPv4 – NAT works around the fundamental IPv4 address shortage, delaying the adoption of better IPv6 addresses.
- Loss of peer-to-peer services – Peers behind distinct NAT devices cannot directly communicate without relay servers.
- Centralized dependency – Internal clients lose Internet access if the NAT device is disrupted.
- Violates IP routing principles – NAT obscures addresses and ports, conflicting with IP’s end-to-end transparency.
- No security in private networks – NAT does not protect against attacks originating from the local network.
- Logging and privacy concerns – Centralized NAT logs reveal who devices are communicating with externally.
NAT and VPCs
In cloud computing platforms like AWS and Azure, Virtual Private Clouds (VPCs) act like an on-premises private network.
Instances inside the VPC are assigned private IP addresses like traditional private networks.
NAT Gateways or Azure Firewall with SNAT provide outbound Internet connectivity for the instances while protecting direct access to them from the public Internet.
Load balancers map the private instances to public IP addresses and ports to enable inbound Internet connectivity to the private instances when desired.

Conclusion
In summary, NAT enables private IP networks to connect to the public Internet by translating private IP addresses to public IP addresses.
This conserves scarce public IPv4 addresses and provides basic network security.
However, NAT breaks end-to-end connectivity, introducing complexity for applications to establish and maintain connections through NAT devices.
As the Internet transitions fully to IPv6, the need for NAT will eventually diminish. In the meantime, NAT traversal techniques enable necessary communication between endpoints across NAT boundaries.
Understanding how NAT works and its tradeoffs allows effective use of this transitional connectivity technology.
Frequently Asked Questions (FAQ)
Ques 1: What is NAT traversal and why is it needed?
Ans: NAT traversal refers to techniques for establishing and maintaining Internet protocol connections in the presence of NAT devices.
It is needed because the IP address translation performed by NAT breaks end-to-end connectivity between hosts located behind distinct NAT devices.
Applications use NAT traversal to enable hosts on distinct private networks to communicate directly with each other.
Ques 2: What is hole punching as a NAT traversal technique?
Ans: Hole punching is a NAT traversal technique in which applications try to simultaneously open ports and create NAT table mappings from both communication directions.
This punches a hole through the NAT devices to enable direct connectivity between the applications. Hole punching only works with particular NAT types like full-cone NAT.
Ques 3: How do TURN servers enable NAT traversal?
Ans: TURN (Traversal Using Relays around NAT) servers act as an intermediate relay to enable connectivity when direct peer-to-peer communication fails.
The hosts connect to the TURN server which forwards traffic between them. This enables connectivity across symmetric NAT and firewalls since the hosts are established as clients of the relay server.
Ques 4: What is port forwarding and how does it differ from NAT?
Ans: Port forwarding is a method to allow external devices to connect to specific ports on internal devices through a router or firewall.
It differs from NAT in that it enables inbound connections from any external device, rather than just enabling outbound connections to the Internet from internal devices.
Port forwarding manually maps ports rather than dynamically translating on each connection.
Ques 5: How are VPNs used for NAT traversal?
Ans: Virtual Private Networks (VPNs) encapsulate internal traffic in an additional IP header using the VPN server’s public IP address.
This enables the traffic to get routed to the VPN server through NAT devices.
The VPN server then forwards the original traffic to the intended public destination or the other side of the VPN tunnel. This traversal technique creates an encrypted tunnel through the NAT devices.