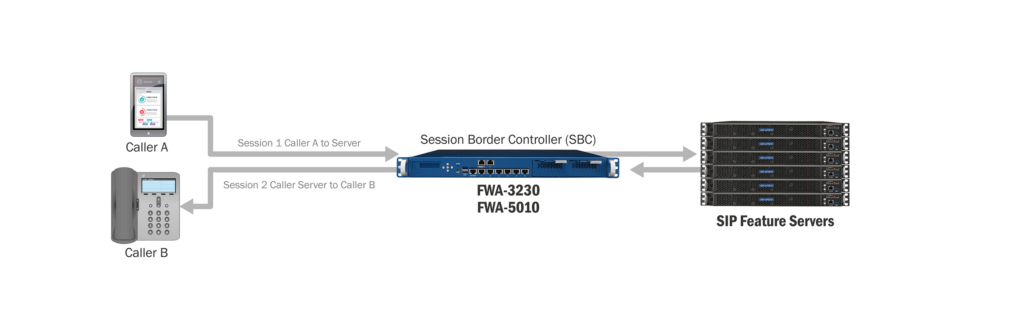
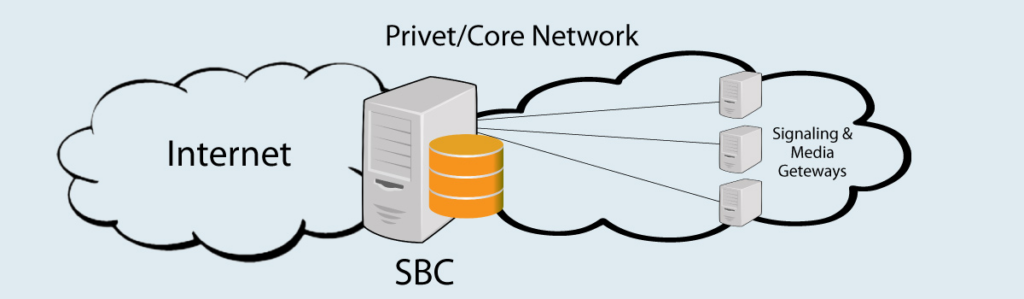
A session border controller (SBC) is a key device that helps enable this. An SBC sits on the border between an internal network and external networks like the Internet.
It acts as a gateway and firewall to manage and control the audio, video, and data sessions that cross between these networks. SBCs provide security, interoperability, and quality of service.
They protect against denial of service attacks, fraud, and eavesdropping. SBCs also enable seamless connectivity between different protocols and networks.
With the rise of unified communications and remote workforces, SBC adoption continues to grow.
This article will explore what SBCs are, how they work, deployment tips, their benefits, and frequently asked questions.
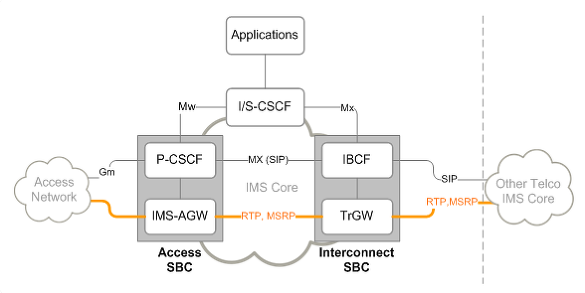
Functioning of Session Border Controller
- Security – SBCs protect internal networks from external threats like denial of service attacks, fraud, eavesdropping, and more. They act as a firewall and block unauthorized access. SBCs use encryption, access control lists, and other mechanisms to secure signaling, media, and data traffic.
- Interoperability – SBCs enable interworking between different protocols, codecs, or vendor equipment. This allows seamless connectivity between disparate systems and networks. For example, an SBC can connect a SIP-based IP PBX to an H.323 video conferencing unit.
- Quality of Service – SBCs manage QoS levels by prioritizing mission-critical traffic like voice and video. They provide traffic policing, call admission control, and bandwidth management to ensure optimal service quality.
- Topology Hiding – SBCs conceal the internal network architecture from outsiders. This provides an additional layer of security and privacy.
- Monitoring & Recording – SBCs can generate CDRs for billing purposes. They also support lawful interception capabilities required by regulatory policies.
- NAT Traversal – SBCs traverse NAT firewalls and enable media connectivity for remote or mobile endpoints. This simplifies network topologies.
- Regulatory Compliance – SBCs ensure networks adhere to telecom regulations, laws, and standards. This includes emergency call handling, lawful interception, and more.
Overall, SBCs act as the middleware connecting internal and external networks.
They enable secure, high-quality communications while abstracting the network complexity.
How a Session Border Controller Works?
SBCs are deployed at the border between the internal and external networks. Here is how SBCs work:
- Media Traffic Handling: When endpoints in different zones need to establish a call or media session, signaling and media flows traverse through the SBC. The SBC acts as a middleman, terminating and then re-originating these flows on either side. This enables the SBC to inspect, monitor, and manipulate the sessions.
- Signaling Protocol Interworking: Suppose the internal IP PBX uses SIP signaling while the external network uses H.323. The SBC seamlessly converts between these protocols, enabling interoperability. Protocol interworking works for SIP, H.323, MGCP, Skinny, and more.
- Codec Transcoding: If the endpoints don’t support a common codec, the SBC can convert between different voice and video codecs on the fly. This ensures users can communicate without being limited by codec incompatibility.
- Security Functions: The SBC applies firewall policies to filter out unauthorized traffic. It blocks denial of service attacks, SPAM over IP, and eavesdropping attempts. Encryption and authentication protect signaling and media.
- QoS & Traffic Control: The SBC classifies and prioritizes real-time traffic while rate limiting or blocking unwanted flows. Call admission control prevents oversubscription of network bandwidth.
- NAT Traversal: The SBC manipulates IP addresses and port numbers using NAT to enable media connectivity for remote endpoints across firewalls.
- Monitoring & Recording: The SBC generates call detail records (CDRs) and can replicate media flows for lawful interception if required by laws.
- Network Abstraction: The SBC hides the internal network topology and masks private IP addresses. This provides a layer of abstraction for enhanced security.
The SBC juggles these critical functions simultaneously for all the media sessions traversing between the network zones.
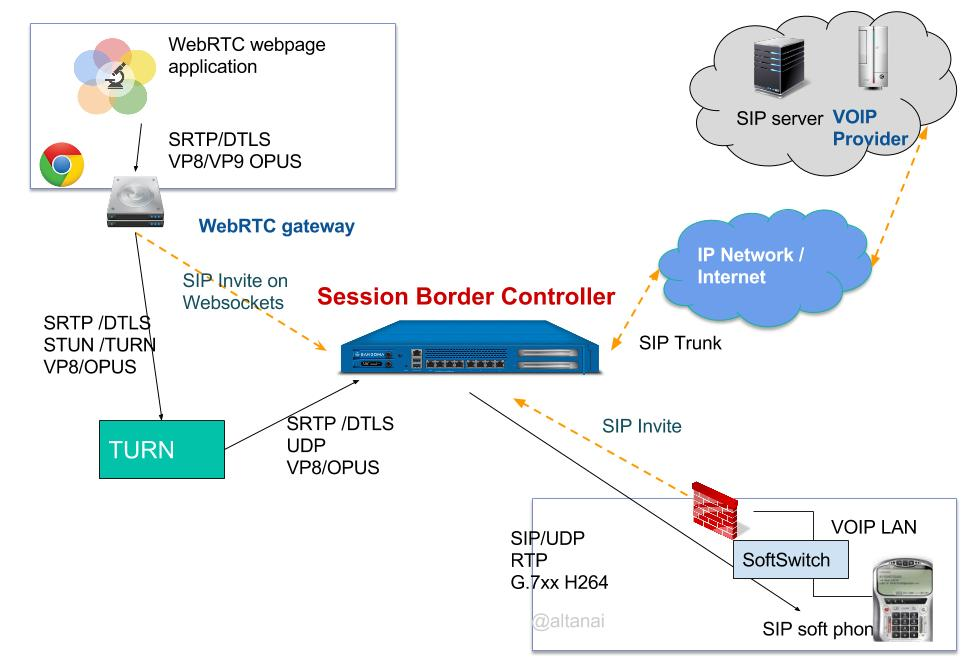
How to Deploy an SBC?
Here are some tips on deploying an SBC:
- Position the SBC at the demarcation point between the internal IP network and external networks like the Internet or B2B partner links.
- Deploy SBCs in pairs in a redundant configuration for high availability. If the primary SBC fails, the backup takes over immediately.
- Scale capacity by adding multiple SBCs behind a load balancer to distribute traffic. Monitor utilization levels.
- Enable security features like encryption, access control, NAT, and topology hiding based on your requirements.
- Configure protocol interworking policies based on the types of endpoints or networks that will interconnect.
- Set up codec transcoding rules to define which codecs to use if endpoints don’t support a common codec. Prioritize high-quality codecs.
- Classify real-time traffic and enable QoS marking to prioritize voice and video traffic. Apply rate limits to prevent congestion.
- Use an SBC with appropriate throughput capacity and scalability to handle your media session load. Monitor traffic regularly.
- Maintain the SBC software up-to-date with the latest stable vendor release. Keep configurations backed up.
- Leverage vendor professional services to assist with installation, configuration, testing, and deployment.
Careful SBC placement, design, configuration, and monitoring help realize the full benefits.
Work with your vendor or network architect for SBC sizing and deployment tailored to your specific needs.
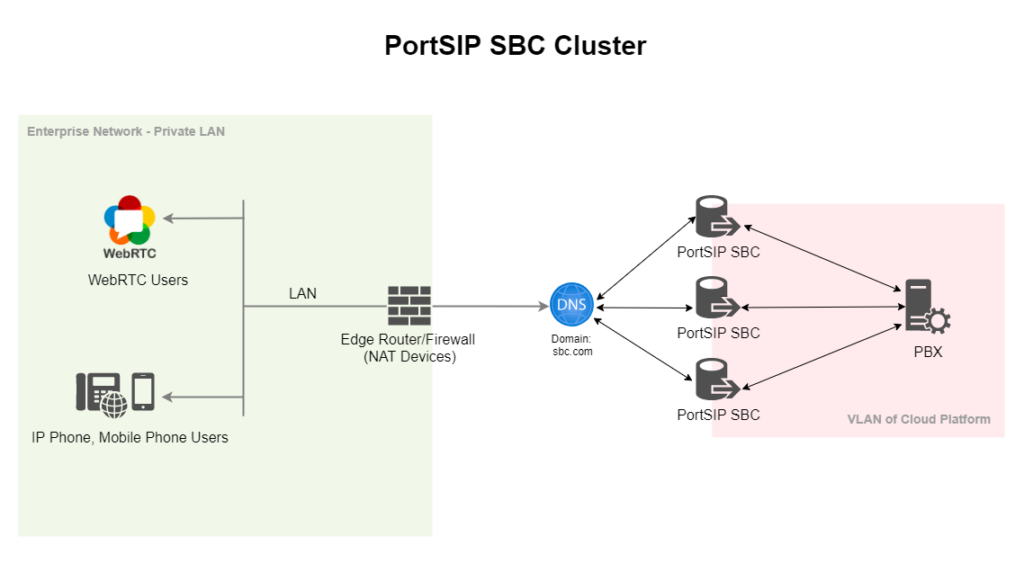
Understanding Session Border Controllers
Here are some key points for understanding what SBCs are and how they benefit communications networks:
- SBCs are not the same as firewalls. Firewalls focus on allowing/blocking network traffic based on IP addresses and ports. SBCs operate at the application layer to manage real-time media sessions.
- SBCs enable connectivity between SIP and H.323 environments. They interwork between VoIP signaling protocols to bridge islands of interoperability.
- SBCs allow VoIP and video traffic to successfully traverse between IPv4 and IPv6 networks. They also traverse between TDM and IP.
- SBCs enable connectivity for remote or mobile workers across the Internet by overcoming NAT and firewall obstacles.
- SBCs protect your critical communications infrastructure from external threats and vulnerabilities with layered security mechanisms.
- SBCs provide fine-grained control over media sessions, including call admission control, bandwidth policing, and QoS marking.
- With an SBC, you can monitor and record calls for generating accurate billing records and to assist with compliance requirements.
- SBCs simplify your network architecture by hiding internal details from the outside world. They prevent direct IP connections through NAT.
- Leading SBC vendors include AudioCodes, Cisco, Oracle, Ribbon Communications, Avaya, and more. Models vary from software to hardware appliances.
- While complex under the hood, SBC configurations can be managed through intuitive web GUIs, command lines, or automation frameworks.
- SBCs evolve continuously to support new protocols, security threats, and use cases as communications technology advances.
Understanding these key differentiators helps appreciate the value SBCs provide for connecting real-time media systems securely and reliably.
Should Your Network Employ an SBC?
Here are some factors to consider when deciding if your network could benefit from deploying a session border controller:
- Are you connecting your VoIP or video infrastructure to external networks like the PSTN or Internet? SBCs securely bridge these environments.
- Do you need to interconnect communication systems that use different protocols like SIP, H.323, or SCCP? An SBC can seamlessly interconnect them.
- Does your network need protection against denial of service attacks, eavesdropping, or unauthorized access? SBCs offer a layer of security.
- Do remote or mobile workers struggle to make voice or video calls due to NAT traversal issues? An SBC facilitates NAT traversal.
- Do you need to monitor calls for billing, quality tracking, or lawful interception purposes? SBCs enable recording and monitoring.
- Does your network need to support connectivity globally between regions that use different codecs? SBCs transcode codecs.
- Are you deploying IP phones over low-bandwidth WAN links? An SBC can prioritize voice traffic.
- Does your network need to comply with emergency call handling, law enforcement agency access, or regulatory mandates? SBCs help meet compliance requirements.
- Are you consolidating multiple disparate voice and video networks? An SBC can unify multi-vendor environments.
If your organization answered yes to any of these use cases, deploying an SBC may provide significant benefits for your network’s boundary security, performance, availability, and flexibility.
Frequently Asked Questions (FAQ)
Ques 1: Why do I need an SBC if I already have a firewall?
Ans: Firewalls perform network layer access control based on IP addresses and ports. SBCs enable application layer signaling and media control for real-time sessions.
SBCs also handle protocol interworking, QoS, monitoring, and other functions firewalls don’t support. Use SBCs and firewalls together for defense-in-depth.
Ques 2: Can I use a softswitch or IP PBX instead of an SBC?
Ans: Softswitches and IP PBXs focus on internal call control. SBCs secure the network boundary between internal and external networks. You can deploy an SBC with a softswitch or IP PBX to protect the edge.
Ques 3: Where should I deploy SBCs in the network?
Ans: Deploy SBCs at the edge, at the demarcation point between the internal network and external networks. Use redundant SBC pairs for failover. Also, deploy SBCs where different network segments interconnect.
Ques 4: Does an SBC affect call quality?
Ans: An SBC can improve call quality by prioritizing real-time traffic, preventing bandwidth oversubscription, and transcoding between codecs. However, excessive transcoding can degrade quality if not configured properly.
Ques 5: What protocols do SBCs support?
Ans: Leading SBCs support SIP, H.323, MGCP, Skinny, TDM, WebRTC, and more. They interwork between these protocols to bridge voicemail systems, video conferencing, IP PBXs, cloud services, and other environments.